Partners: Talk to Your Customers About Ransomware Now


Ray White
 If you haven’t talked to your customers about data security and ransomware attacks that can occur when employees work from home, now is the time. Businesses large and small are facing a host of new challenges because of COVID-19. Without much advance notice, many have been asked to work from home for an undetermined amount of time. Now that businesses are embracing remote work, we have discovered new infrastructure implications of deploying enterprise-grade end-user computing such as scale, performance, and security. The most challenging is security, because of the rise of ransomware.
If you haven’t talked to your customers about data security and ransomware attacks that can occur when employees work from home, now is the time. Businesses large and small are facing a host of new challenges because of COVID-19. Without much advance notice, many have been asked to work from home for an undetermined amount of time. Now that businesses are embracing remote work, we have discovered new infrastructure implications of deploying enterprise-grade end-user computing such as scale, performance, and security. The most challenging is security, because of the rise of ransomware.
Working from Home? Be Aware of Security Risks
According to reports from data security company Emsisoft, ransomware is costing businesses, hospitals, schools, and government agencies billions. In 2019, Emsisoft reported that ransomware hit more than 120 state and municipal governments and agencies, 764 healthcare providers, and 89 universities, colleges, and school districts (affecting potentially more than 1,000 individual schools).I have been monitoring internet traffic since the mid-1990s and I have never witnessed the amount of internet traffic we are seeing due to COVID-19 and working from home. For ransomware, this kind of chaos is opportunity. Just check out the Internet Live Stats and Internet Traffic Report traffic maps.
Ransomware is on the rise and targeting not only critical infrastructure systems, but also backup systems and endpoint devices. Here is a map of global internet attacks in real time.
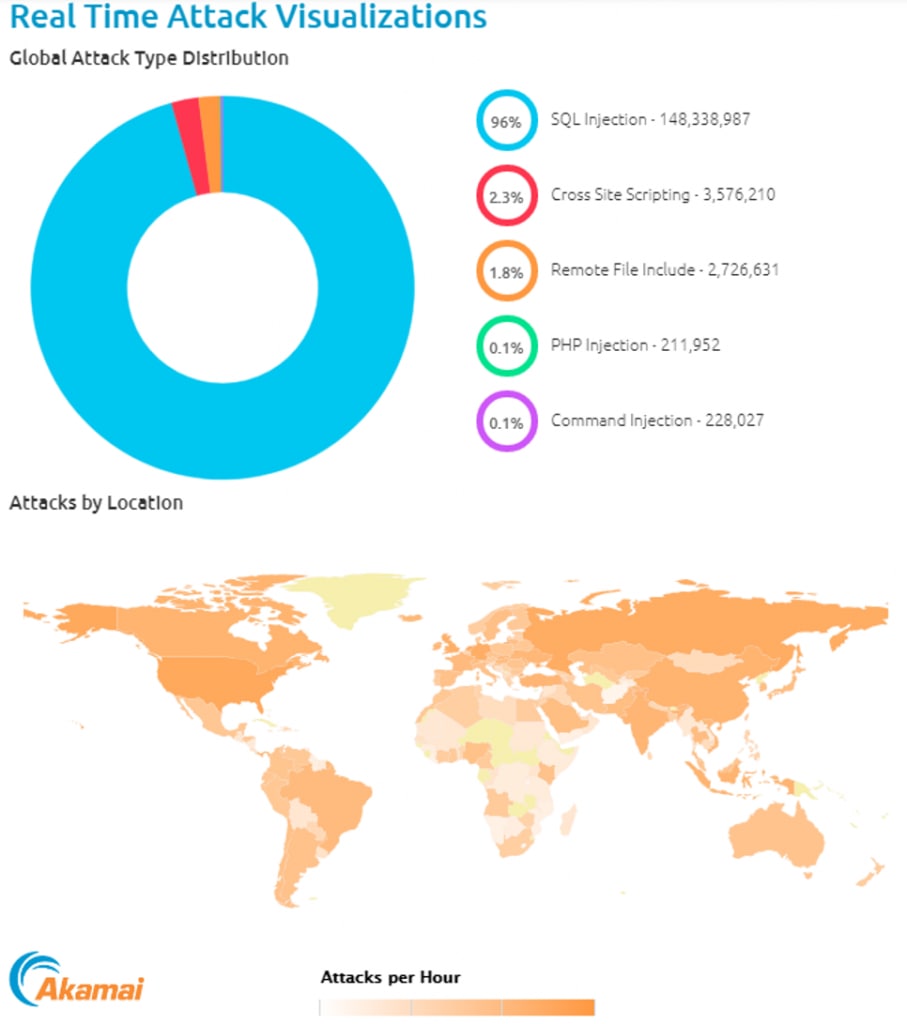
Ransomware Is a Major Threat to Both Enterprises and Individuals
Ransomware aims to take control of sensitive data and disrupt businesses across the globe. It is a product of organized crime, and the attackers do not operate ethically. Ransomware is a type of malware that is based on cryptology, which is the use of cryptography to build malicious software. Cryptographic methods enable the encryption of data with a shared secret key (symmetric key encryption) or a pair of keys (asymmetric key encryption). One of these keys is a widely available public key and the other is an undisclosed private key. This malware can use both symmetric and asymmetric key encryption to lock a victim’s data and demand a ransom to provide the key to decrypt the data.They can refrain from providing a decryption key even after receiving the ransom. The victims lose not only their data but also a substantial amount of money, and they face consequences associated with the loss of production data. According to a Forbes article, only 19% of ransomware victims get their data back after paying the ransom. Therefore, the authors recommend not paying a ransom, because paying it reinforces the attacker’s faith in this business model.
Safeguarding Your Business
What if you could safeguard your business from these malware attacks by taking advantage of existing technologies across the storage, network, and compute layers?At NetApp, we have always taken a security-first approach. We believe that security features to harden your environment should be enabled by default and in an “always-on” state. Data security should not be an afterthought and should not affect infrastructure performance.
Today, NetApp offers a portfolio of encryption and security options, regardless of whether your data is at rest or in flight. These options include software encryption through built-in cryptographic modules, self-encrypting hard drives, aggregate encryption, volume encryption, and WORM (write once, read many)—that is, the ability to write your data once, locking it in place so it can be read many times.
Our solutions help customers solve numerous security problems. For example, our customers need to harden their critical electronic information. And they need to be sure that their environments are using best practices and features from the security industry to protect their data, the lifeblood of their business.
Anyone—from individuals to large organizations—can be attacked by ransomware. Organizations that do not implement well-defined security measures and practices are even more vulnerable to such attacks. The effect of an attack on a large organization can be several times more serious than what an individual might endure.
What Is Your Ransomware Strategy?
Recovering from a ransomware attack with minimal downtime is possible only by implementing a proactive disaster recovery plan. Being able to recover from an attack is good, but preventing an attack altogether is ideal. Although there are several fronts that you must review and harden to prevent an attack, the core component that allows you to prevent or recover from an attack is the data center. You must understand where your data resides, and you must control access to it. Protecting your data at the storage layer is critical.If your data is the lifeblood of your business, why not protect the vault?
How to Continue Business Operations Without Paying Ransom
The data center design and the features it provides to secure the network, compute, and storage endpoints play a critical role in building a secure environment for day-to-day operations. For an example, read FlexPod, the Solution to Ransomware to learn how a FlexPod® hybrid cloud infrastructure can help you recover data quickly after an attack and can help prevent attacks altogether. Also check out our Security Hardening Guide for NetApp ONTAP® 9.Use Active IQ to Detect Potential Security Risks with ONTAP Systems
NetApp Active IQ® makes it easy to identify deployed systems with security risks and also provides recommended corrective actions. The Security Vulnerability tab in Active IQ contains information about the specific risk, the potential impact, and affected systems. In the recent Active IQ Digital Advisor release, this information can be found in the Wellness area under Security. For more information about using Active IQ, see the Active IQ Quick Reference Guide on the Field Portal/Partner Hub.Data-at-Rest Encryption Solutions in ONTAP 9
All ONTAP 9 systems have three FIPS 140-2–compliant data-at-rest encryption solutions:- NetApp Storage Encryption (NSE) is a hardware solution that uses self-encrypting drives.
- NetApp Volume Encryption (NVE) is a software solution that lets you encrypt any data volume on any drive type where it is enabled; it uses a unique key for each volume.
- NetApp Aggregate Encryption (NAE) is a software solution that lets you encrypt any data volume on any drive type where it is enabled; it uses unique keys for each aggregate.
We’re Here to Help
At NetApp, we believe that your environment should be hardened to protect against a ransomware attack. The issue today is not if but when your organization will be affected by ransomware. We are here to help you during this tough time.The data center design and the features it provides to secure the network, compute, and storage endpoints play a critical role in building a secure environment for day-to-day operations. As a call to action, read FlexPod, the Solution to Ransomware to learn how a FlexPod® hybrid cloud infrastructure can help you recover data quickly after an attack and can help prevent attacks altogether. Also check out our Security Hardening Guide for NetApp ONTAP® 9.
Ray White
Ray White is a Datacenter pursuit manager supporting the Cisco Systems Alliance in the Americas at NetApp Inc. With revenues of $6.15 billion in 2019 and 10,000 employees worldwide, NetApp is a global leader in enabling businesses and service providers to transform their operations and deliver IT as a service. Fundamental to this transformation is cloud computing. Through innovative products and services, NetApp accelerates the journey to cloud computing, helping IT departments store, manage, protect and analyze their most valuable asset—information—in a more agile, trusted and cost-efficient way. Ray has more than 21 years of industry experience in information technology software, hardware and sales and services. Working at NetApp since 2005, Ray has achieved the highest levels of consistent performance and contribution throughout his tenure in both sales and technical leadership. Prior to NetApp Ray was a leader and engineer at major service provider, Road Runner, during the internet boom. Ray is an expert in Cyber security, advanced networking, software development and all things Artificial Intelligence.
