Fighting Ransomware: Part Four – UBA and ONTAP with FPolicy External Mode


Matt Trudewind
 Suppose that you are a chief information security officer (CISO), chief technology officer (CTO), or IT manager, with responsibility for all the information systems in your organizations. Your team applies security patches to software and applications as soon as they come out. You’re not worried about viruses or malware, because, along with your blistering speed at patching, you have a solid firewall, up-to-date antivirus scanning, and a solid VPN strategy for remote access. So, you might be shocked when you and everyone in your company logs in to discover something like this on the screen:
Suppose that you are a chief information security officer (CISO), chief technology officer (CTO), or IT manager, with responsibility for all the information systems in your organizations. Your team applies security patches to software and applications as soon as they come out. You’re not worried about viruses or malware, because, along with your blistering speed at patching, you have a solid firewall, up-to-date antivirus scanning, and a solid VPN strategy for remote access. So, you might be shocked when you and everyone in your company logs in to discover something like this on the screen: 
One of the most likely causes for this scenario is a zero-day ransomware attack. These attacks are based on the concept of a zero-day vulnerability, which Norton defines as “a software security flaw that is known to the software vendor but doesn’t have a patch in place to fix the flaw. It has the potential to be exploited by cybercriminals.” Basically, there was no patch available for the type of ransomware used to infect this security-conscious organization. To complicate matters, the software vendor might not even be aware of the flaw. However, there is still a way you can protect your business from zero-day ransomware attacks using NetApp® FPolicy, our Zero Trust engine, in external mode.
This blog post is the fourth in a six-part series that covers how you can detect and prevent ransomware by using native NetApp® ONTAP® features, recover quickly from an attack, and avoid paying the ransom. It’s best to read them in chronological order:
- The first entry covered the objectives of cybercriminals and the largest portion of the cost of a ransomware attack, which is not the ransom.
- The second entry is focused on ONTAP native tools that you can use for early detection of a ransomware outbreak.
- The third entry took a deep dive into NetApp FPolicy® native mode, which helps prevent most older types of ransomware that are still prevalent today.
- The fourth entry is focused on how to prevent the most modern variants of ransomware, including “zero-day” exploits, by using FPolicy external mode.
- The fifth entry highlighted the three key steps to successfully recover from a ransomware attack.
- The sixth entry focused on ONTAP Snapshot technology and how it provides very rapid restores (terabytes in seconds, not hours), protects your backups from ransomware encryption, and prevents deletion of valuable backup data.
What Is User Behavioral Analytics (UBA)?
FPolicy external mode in ONTAP uses UBA (sometimes referred to as “User and Entity Behavior Analytics,” or UEBA) as the key to stopping a zero-day ransomware attack. To understand how, you need a solid understanding of UBA.Human beings are creatures of habit. Our habits apply to many things, including how we access and work on data. Users and groups often access particular datasets to perform their jobs. UBA tracks these behaviors, identifies typical access patterns for a user, and can report when that user’s behavior differs from the pattern. Going a step further, UBA can also deny access to file data if users are doing something outside their usual patterns. FPolicy external mode integrates with an external server that uses UBA to determine when users are doing things they don’t normally do.
In the following example of a security information and event management (SIEM) system, every CIFS or NFS client request is sent to the FPolicy server, which judges whether the access should be allowed.
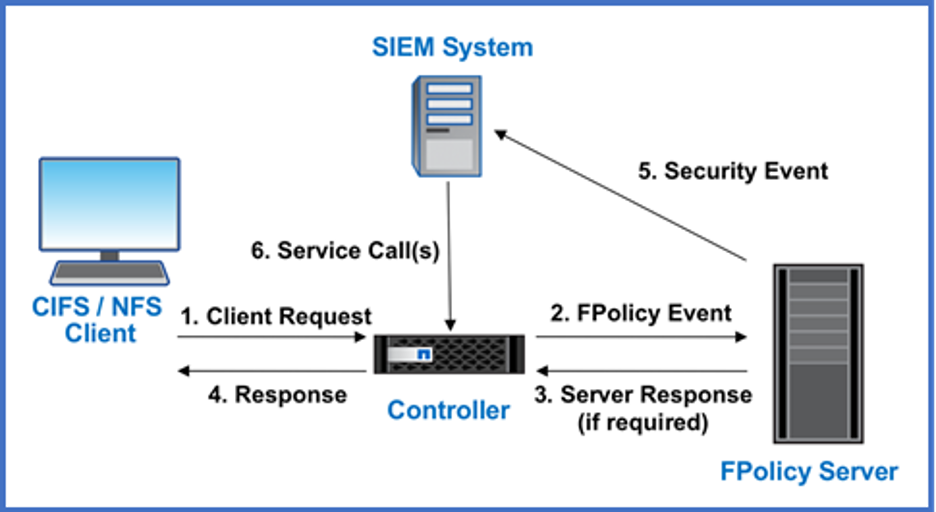 This extra level of analysis occurs even if users have file permissions to the file data they are trying to manipulate. Because permissions are hard to get right all the time, UBA with FPolicy can be a much better gauge in determining whether the user is trying to do something nefarious. You can learn more about UBA in the NetApp technical report NetApp and Zero Trust.
This extra level of analysis occurs even if users have file permissions to the file data they are trying to manipulate. Because permissions are hard to get right all the time, UBA with FPolicy can be a much better gauge in determining whether the user is trying to do something nefarious. You can learn more about UBA in the NetApp technical report NetApp and Zero Trust.
UBA is quite powerful, but it’s not the end game in fighting against zero-day ransomware attacks. Many NetApp partners and vendors have started to incorporate artificial intelligence (AI) and machine learning (ML) in their external FPolicy servers. Because each vendor plugs into the FPolicy feature built into ONTAP, these AI/ML enhancements can be harnessed right away.
How Do I Obtain an External FPolicy Server?
The external FPolicy server runs outside ONTAP; hence the “external” name. But how do you find one? NetApp has partners that integrate with the ONTAP FPolicy feature. You can find more details about these partners on the NetApp Partner Connect site. Each partner has its own recommendations and best practices for configuring the FPolicy server to work with the ONTAP FPolicy feature. There is no one-size-fits-all approach for installing and configuring the third-party external FPolicy server. Some partners also handle the UBA/AI/ML portion differently. As a result, it’s important to explore each partner’s solution to determine which one best fits your needs.
You can find more details about these partners on the NetApp Partner Connect site. Each partner has its own recommendations and best practices for configuring the FPolicy server to work with the ONTAP FPolicy feature. There is no one-size-fits-all approach for installing and configuring the third-party external FPolicy server. Some partners also handle the UBA/AI/ML portion differently. As a result, it’s important to explore each partner’s solution to determine which one best fits your needs.
Note: Although the NetApp FPolicy feature that integrates with a partner solution is built into ONTAP at no additional cost, the partner’s solution is not included and represents an added cost.
You’ll also notice that NetApp Cloud Insights is listed with FPolicy partners in the graphic above. At the NetApp INSIGHT® 2019 conference in Las Vegas, NetApp announced that Cloud Insights can include an external FPolicy server by using the NetApp Cloud Secure component. So, you can have a fully native NetApp solution that uses Cloud Insights. To learn more, see the Cloud Insights page.
Even though each partner’s external FPolicy server has its own unique configuration, the ONTAP portion for external mode setup is very similar among partners.
ONTAP Configuration in FPolicy External Mode
In the previous blog, we discussed how to set up whitelist and blacklist rules for protecting your files from ransomware. With ONTAP FPolicy external mode, the whitelist and blacklist portion is configured on the partner server. Most partner servers automatically update their blacklists as new ransomware signatures become known. It’s similar to how your antivirus clients get new virus definitions. The difference is that, with the partner FPolicy server, you aren’t relying on these signatures alone. You also have the UBA/AI/ML portion that covers the new attacks that software and security companies do not yet have signatures for.Even though the configuration is being handled on the external server, you still need to configure ONTAP to interface with the partner’s FPolicy server. Here is an example of creating that external server connection from the CLI.
Note: It’s important to check the documentation from NetApp and from the external FPolicy server provider for specific configuration details. Use the following steps only as a general guide.
- Create a new FPolicy event and specify the storage virtual machine (SVM) it will run against, the file protocol (NFS or CIFS), the types of file operations it applies to, and the filters used with the file operations.
- Create an FPolicy external engine and specify the partner server’s IP address, the port it is listening on, the authentication method, and the engine type (synchronous or asynchronous, depending on the vendor).
- Create a new policy; specify the event you created in step 1, and specify that the policy should use the external FPolicy engine.
- Assign the file scope—that is, which volumes to include (I recommend using a wildcard for all volumes) and which file shares or exports to include in the policy. In the following example, we are specifying a share because the policy applies to the CIFS protocol.
- Enable the policy and assign the appropriate priority in case multiple policies are being configured.
- Verify the configuration by using the vserver fpolicy policy scope
Vserver: svm1 Policy: fp_external_policy Shares to Include: * Shares to Exclude: - Volumes to Include: * Volumes to Exclude: - Export Policies to Include: - Export Policies to Exclude: - File Extensions to Include: - File Extensions to Exclude: - Is File Extension Check on Directories Enabled: false Is Monitoring of Objects with No Extension Enabled: false
In this example configuration, all shares and volumes on SVM1 are now being monitored by the external FPolicy server. They are protected from ransomware and zero-day ransomware attacks by harnessing the power of UBA/AI/ML in the external FPolicy server.
What to Do If You’re Still Hit with a Ransomware Attack
Since the beginning of this blog series, I’ve focused on ways to detect and prevent ransomware. The primary goal is to avoid infection. FPolicy external mode is perhaps the most powerful tool in the arsenal to prevent ransomware attacks. However, the reality is that no prevention strategy is 100% foolproof. In addition, you might have been hit with an attack before you had a prevention plan in place. That’s why the next blog in this series will shift the focus to the worst-case scenario: an attack has already occurred. I’ll show how you can quickly recover from a ransomware attack and remediate by using the leading capabilities in ONTAP. If you would like to get a jumpstart or learn more about the NetApp solution to ransomware, check out our technical report, TR-4572: The NetApp Solution for Ransomware.Plus, want to learn how you can further protect your organization with NetApp’s leading security portfolio? Check out our ONTAP Security webpage for information on using a data centric zero trust approach to security, evaluating your security readiness, encrypting your data at rest or in flight, and more.
Matt Trudewind
Now on his 2nd tour at NetApp across 10 years, Matt is a Security Evangelist with a primary focus on ransomware prevention and recovery, cyber resiliency, and data-centric portfolio security. This includes but is not limited to Zero Trust, Data Governance and Privacy Frameworks, Security Tools, and Security Best Practices. Prior to this Matt held the dual role of Product Manager and Technical Marketing Engineer for ONTAP Security driving the latest security features and capabilities into NetApp’s flagship product. He has also held the position of Staff Engineer at NetApp during which he focused on ONTAP product Supportability specifically in the areas of networking and SMB/CIFS. In between NetApp stints Matt worked with a NetApp partner (Eze Castle Integration) for 7 years as pre sales/post sales storage architect focusing on early 7-mode to cDOT migration. He has also focused on Microsoft Windows Active Directory, Exchange, SQL and VMware during his 23 years of IT experience with 17 of those years coming in the storage industry. Prior to NetApp and ECI, Matt worked a contract at Microsoft as a Technical Support Engineer.